Cyber threats appear to be everywhere in this digital time. Viruses, malware, ransomware, trojans, phishing and much more make an endless rundown of cyber threats. However, perhaps the most profound threat out there that frequently gets neglected is manipulator- in-the-middle (recently known to as ‘man-in-the-middle’) attack.
While utilizing the web, we anticipate that our communications should be classified and not to be changed or altered while on the way. At the point when you are presenting some sensitive data to a web application, you depend with the understanding that:
- all that you have entered is legitimate,
- all of the data arrives at the server in its right structure, and
- outsiders can’t see, block or change your data.
In any case, the truth of the matter is that a MITM attack (man-in-the-middle) breaks any of the last two presumptions or both. In the event that the connections you make to sites and online administrations are not secure, you could be defenseless against security dangers, for example, phishing, viruses, ransomware, malware and numerous others.
The Start and the Present
Intercepting and modifying communication has occurred for quite a long time, and the appearance of the web and further development has made it simpler than any time in recent memory for cyber criminals to infuse their inclinations into private transmissions.
During the late-sixteenth century, letters identified with an assassination plot against Queen Elizabeth I of Britain by Mary Stuart and her fellow group members were captured, decoded and changed by a cryptography master named Thomas Phelippes. This turns out to be one of the oldest MITM attacks on record.
As of late, the individual data of in excess of 12,000 Indian blood donors were on offer on the web free of charge. It was found by a risk monitoring firm. The break may have been conceivable as a result of an unstable HTTP site that was captured by outsiders or an uncovered data set or cloud storage server, or even a phishing effort that prevailed with regards to getting to system administrator credentials.
MITM attacks generally take two processes:
- The first is the place where a rival might need to read the content of a message which is frequently supposed to be an attack on privacy.
- The second would include the rival changing the content of the message or in any case altering the communication which is supposed to be an attack on integrity.
Sorts of Man-in-the-Middle Attacks
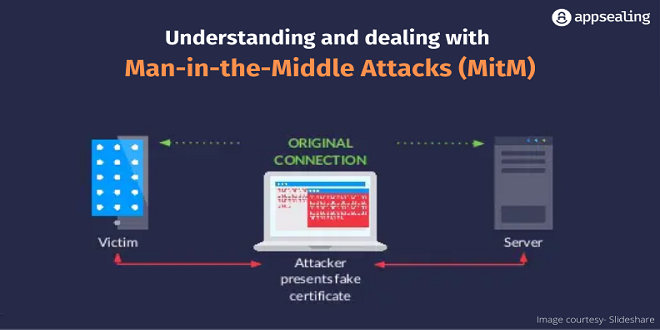
A MITM attack is basically a snooping circumstance wherein an outsider or a rival covertly embeds itself into a two-party discussion to gather or change information. MITM attacks can influence any exchange in communication, including device-to-device communication and connected peripherals (IoT).
For the most part, man-in-the-middle attacks can be classified into two:
Attack on Active Session
During an active session attack, the attacker prevents the first client from speaking with the server and afterward replaces himself inside the session. Starting from there, the attacker will communicate with the server and he will actually want to do anything that an ordinary client can do. He could alter the data or gather sensitive data that might have a potential effect later.
Attack on Inactive Session
In an inactive session attack, the attacker screens the data streaming across the organization without intruding on the genuine communication. The prowler snoops the communication however doesn’t alter the message stream in any way. He could gather all of the data going through the organization which might cause a functioning attack later.
Procedures Utilized in Man-in-the-Middle Attacks
A portion of the average man-in-the-middle attack methods utilized are:
Rogue Access Point
A rogue access point is a device that is working on the organization without the approval of an admin, representing a security danger. They are set up to deceive PCs that consequently interface with Wi-Fi by acting like authentic public networks. These rogue networks regularly screen traffic and take sensitive data. The attacker could utilize this rogue network as a public Wi-Fi of a coffeehouse to control and catch each communication going through that organization.
Spoofing of Address Resolution Protocol (ARP)
ARP is a communication protocol used to discover the MAC address of a specific device whose IP address is known. Assuming a device needs to speak with one more device on the organization, then, at that point, the sending device utilizes ARP to find the MAC address of the device that it needs to speak with. Furthermore, these ARP bundles can be produced to associate with a device as an authentic one which is alluded to as ARP spoofing. This permits the attacker to catch, alter and drop the approaching messages.
Spoofing Domain Name System (DNS)
Domain Name System (DNS) spoofing is a procedure that deceives a client to a false site rather than the genuine one the client expects to visit. The site will have all the earmarks of being the genuine one and you might believe you’re visiting a protected, trusted site when you’re really collaborating with a fraudster. The attacker will likely redirect traffic from the genuine site or catch client login credentials and different data.
Hijacking of Email ID
Email hijacking happens when attackers compromise and get to a client’s email record and watch communications to and from the record. Whenever a chance shows up, for example, if the client is trading funds or some other data with another party, the attacker exploits the circumstance by aiming to block the funds and move it to their own records. Attackers can likewise utilize the email to take over other internet based records attached to the email account.
Redirection of Internet Control Message Protocol (ICMP)
ICMP is utilized by network devices, similar to switches, to speak with the source of a data packet about transmission issues. For instance, it may answer to the host that a mentioned administration isn’t accessible or that a host or switch couldn’t be reached. To build up a fruitful MITM attack, the attacker searches for the hosts that are down. At the point when these hosts are pinged by different hubs in the organization, the attacker will react to them by sending a successful ping message.
Appsealing helps individuals and companies by stopping these MiTM attacks and other security concerns related to a business.