Environment configuration
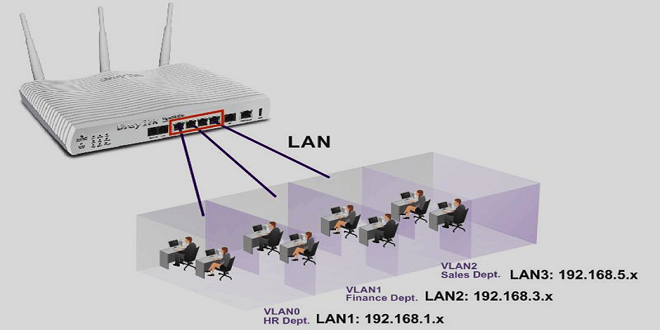
The following content uses a certain type of layer-3 switch as an example, for example, a 24-port 100M layer-3 switch, and VLAN technology is applied to this switch. Switch1 is mainly responsible for the first three ports, and Switch2 is mainly responsible for the last three ports. We set the Tag value of VLAN1 to 10; at the same time, the last three ports of Switch1 can be compared with the last three ports of Switch2. It is set to VLAN2, and at this time we set the Tag value of VLAN2 to 20; this is to connect the switch ports that the two models want to use with each other, and use two different network switches to connect the Tagged ports, then we get The Tag values are 10 and 20.
Data flow
In the data flow, if PC1 sends a data request to PC2, then the first port is mainly an ordinary Ethernet card, so what it sends out is the most standard data frame. At this time, after Switch1 receives the data, it can insert the Tag value in the process of data transmission, so that it can play a corresponding role, and after the insertion, the data segment needs to be kept in the VLANID. In the process of finding data, the switch also needs to combine the local FDB table to find certain items, provide an exchange basis for data information transmission, and ensure that it can appear in the 24th port. The main reason is that the 24th port is the final The content of the information will be sent to VLAN1, so the data can be delivered. Witch1 transmits the data to be transmitted to Switch2 through the port, but at this time the content of the data needs to be marked to ensure that the content can be found at the first time when a conflict occurs. At this time, after the data information received by Switch2 is guaranteed to be digitized, it will be classified according to the classification of the data content, and sent to the specified target port in the form of marking, and then the value of its data transmission will be set to 10, and finally Implement forwarding function in VLAN. switch2 needs to forward the specified content to the specified location according to the FDB address table entry, and finally connect it with PC2, let it appear on the port of Switch2 and finally be transmitted to VLAN1, where all kinds of data are transmitted to port 1, the switch All marked data will be removed and finally received at the designated port.
Configure VLANs
By default, a Layer 3 switch can meet the requirements of various VLANs within the network, and create VLANs through commands. When creating a VLAN, you also need to create an ID. This content can support a maximum of 4096, and it can work between multiple. In the process of adding ports, there are two main ways to add switches, the details are as follows: IEEE802.1QTagged mode and IEEE802.1QUntagged mode.
All VLANs in the same range belong to the same area. After joining the VLAN, this mode can be added to the ordinary port. If it is a trunk port, IEEE802 support is required to configure the corresponding port. Adding the port Jobs also require commands to be added.
In the specified IP address, the three-layer switch can work in the same VLAN, and can also work in different areas in a network. In this process, the IP can cover it and issue commands while covering it. During the configuration process, the host needs to set it as the default network, and complete the required configurations through the port connection address of the layer-3 switch, so as to realize the role of VLAN, and also need to ensure whether the network can be connected.
Conclusion
To sum up, the current development of Layer 3 switches in China has become the main direction of the network scale. At the same time, people are paying more and more attention to VLAN technology. Based on this, we should also give full play to its advantages to meet People’s network needs, and in the process, improve the security issues of Ethernet, on the basis of ensuring security issues, apply this network, and when the technology matures, apply it in more fields, let it be a network The industry provides support, and finally realizes the scale and standardization of network construction and improves network development.